S.H.E.L.L. CTF
anonymCollide
EASY-RSA
encoder
Fun with Tokens
haxxor
login
Under Development
anonym
Category: Web
Description
Anonymous are back and they really hate robots.
Solution
We can take a hint from the description and look for something connected to robots. The first thing that comes to mind is robots.txt file.
Wikipedia states Robots.txt is a standard used by websites to communicate with web crawlers and other web robots. The standard specifies how to inform the web robot about which areas of the website should not be processed or scanned.
Browse for http://3.142.122.1:8887/robots.txt and find Disallow: /yfhdgvs.txt. Visit given subsite and get the flag
SHELL{n0_ro80t5_4llow3d_50886509749a98ef14ec2bc45c57958e}
Collide
Category: Web
Description
Solution
Our goal is to supply two different parameters (shell and pwn) which hash is the same. Normally, we’ll look for something like Magic Hashes or known collisions, but SHA256 has none of that whatsoever. The values are supplied via GET parameter, so we can control the type of the variable. If we input our variables as arrays, we can bypass the SHA256 check. Our payload looks like this
http://3.142.122.1:9335/?shell[]=x&pwn[]=y
We get our flag
SHELL{1nj3ct_&_coll1d3_9d25f1cfdeb38a404b6e8584bec7a319}
EASY-RSA
Category: [CATEGORY]
Description
n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311 e = 65537 c = 33475248111421194902497742876885935310304862428980875522333303840565113662943528
A file was attached.
Solution
To decrypt the flag we have to get p and q - two factors that multiply to n. Using factor.db we get
p = 31415926535897932384626433832795028841
q = 56129192858827520816193436882886842322337671
Now we have to compute phi = (p-1)*(q-1), d - inverse of e modulo phi and then we can compute our plaintext. Example script in Python:
from Crypto.Util.number import long_to_bytes
import libnum
import sys
def compute_gcd(x, y):
while(y):
x, y = y, x % y
return x
def compute_lcm(x, y):
lcm = (x*y)//compute_gcd(x,y)
return lcm
def decrypt(pk, ciphertext):
#Unpack the key into its components
key, n = pk
#Generate the plaintext based on the ciphertext and key using a^b mod m
plain = [chr((char ** key) % n) for char in ciphertext]
#Return the array of bytes as a string
return ''.join(plain)
n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311
e = 65537
c = 33475248111421194902497742876885935310304862428980875522333303840565113662943528
# from factordb
p = 31415926535897932384626433832795028841
q = 56129192858827520816193436882886842322337671
phi = (p-1)*(q-1)
d = pow(e,-1,phi)
plaintext = pow(c,d,n)
print(long_to_bytes(plaintext))
Our flag
shell{switchin_to_asymmetric}
encoder
Category: Cryptography
Description
can you decrypt this text : “ZOLSS{W1G_D3HY_4_T45R}”
NOTE: do not shift the numbers and the special charecters( ‘{‘ , ‘}’ , ‘_’ ).
Solution
We can notice that same letters in the plaintext (LL in shell) correspond to same letters in ciphertext (SS in ZOLSS). We deduct that it is probably some ROT cipher. Some trial and error and we see that ROT19 gives us good answer
SHELL{P1Z_W3AR_4_M45K}
Fun with Tokens
Category: Web
Description
I have got secret information that this webapp is vulnerable. Did i fail in verifying passwords ? http://3.142.122.1:9334/
Solution
The site contains two links - Admins and Login. For some, simply clicking the links doesn’t work - to get to the subsite you have to change the URL by hand.
In the /login page there is a simple login form. Let’s start BurpSuite to see what happens under the hood. I supplied user and pass as the credentials. Submitting the form brings us back to main page, like nothing happened. BurpSuite however reveals, that we recieved a token in the response

eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImhmcmUiLCJwYXNzd29yZCI6ImNuZmYiLCJhZG1pbiI6InNueWZyIiwiaWF0IjoxNjIzMDQ4NDY4fQ.Zzu_yPrjAIGVJyCCIwRYGWCTbQOg6spD98OVT9bxSik
We can decode it using jwt.io for example.
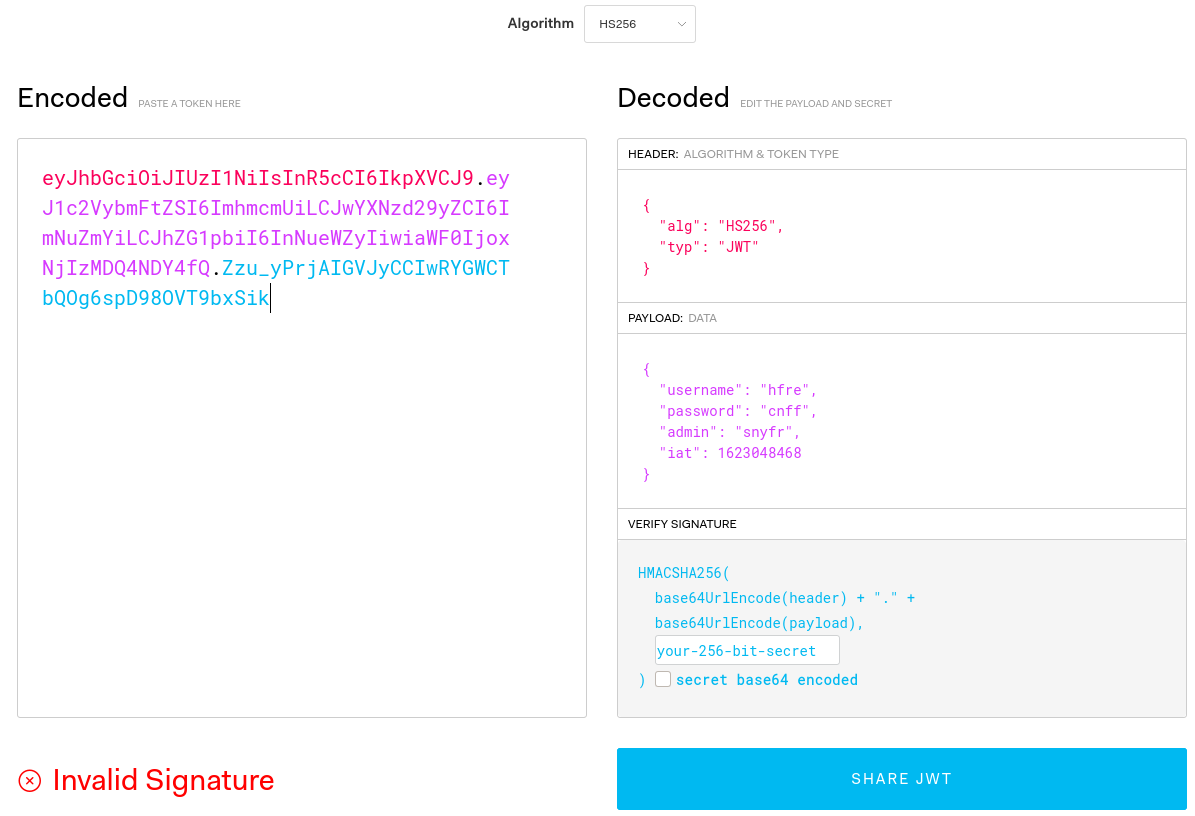
If we decode the username and password in the token with ROT13 we’ll get the credentials we typed in earlier. Decoding snyfr as the “admin” parameter gives false. We still are missing the username and the secret used to sign the tokens.
Inspecting the main page shows us these comments:
<!-- /admin is where the fun's at XD -->
<!--The secret you seek is in the environment-->
Little bit of googling, trial and error and if we input .env as the subsite (http://3.142.122.1:9334/.env) we get this response:
Cannot GET /.env
We somehow have to find a way to download the .env file.
If we enter the /adminNames page, we recieve a prompt for downloading a file containing names of the admins (duh…). BurpSuite reveals that the file name is supplied via a parameter (GET /getFile?file=admins HTTP/1.1). If we switch the file name to ../.env we can download the suspicious document. Open it to get
secret=G00D_s0ld13rs_k33p_s3cret5
Combine all the information we’ve got, ROT13 encode one of the admin usernames (din_djarin11 -> qva_qwneva11), change the admin parameter to true (gehr in ROT13) and supply the secret to get the token
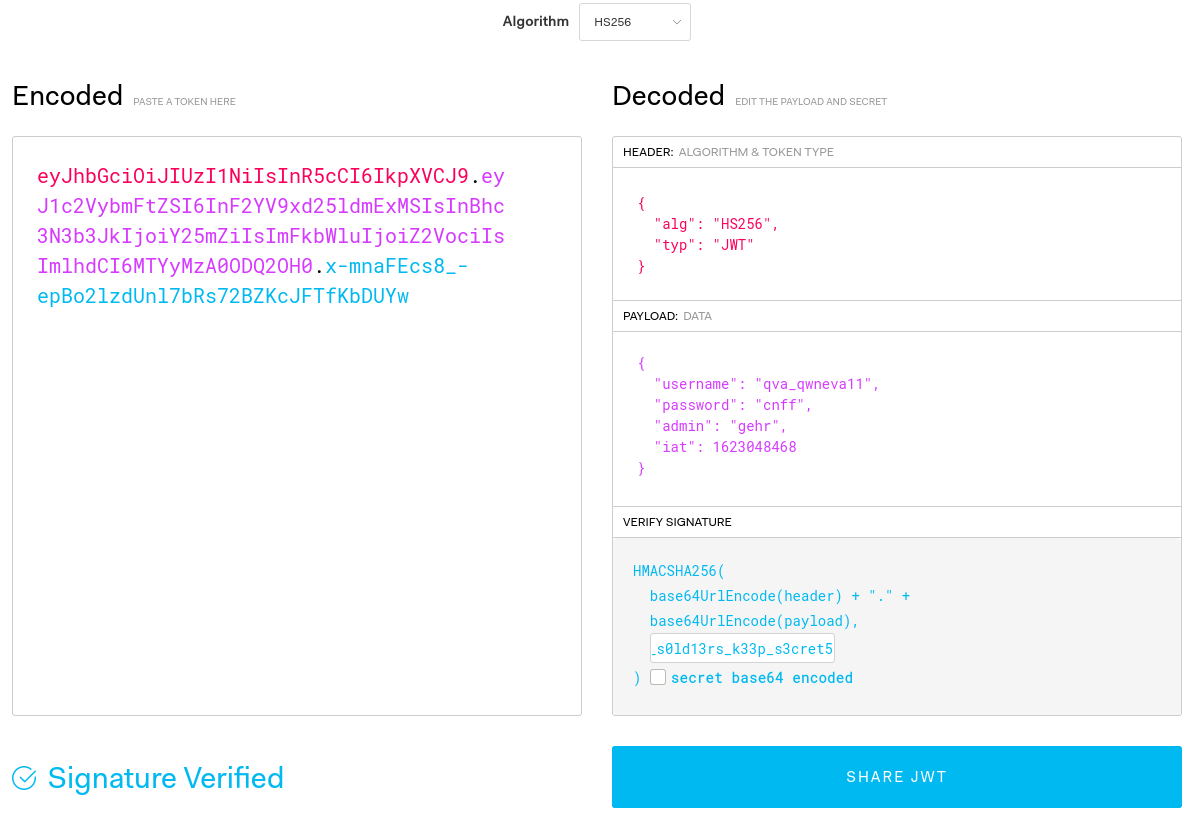
Now, request the /admin subsite, add header
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6InF2YV9xd25ldmExMSIsInBhc3N3b3JkIjoiY25mZiIsImFkbWluIjoiZ2VociIsImlhdCI6MTYyMzA0ODQ2OH0.wRp_JD6wk6bRxffubCPrDQMTcHxVFU8VWl4lcaBQ4i0
and send! (If you have problems with recieving the response, use cURL or Postman). We get the response
Hey din_djarin11! Here's your flag: FURYY{G0x3af_q0_z4gg3e_4r91ns4506s384q460s0s0p6r9r5sr4n}
Decode the flag with ROT13 to get
SHELL{T0k3ns_d0_m4tt3r_4e91af4506f384d460f0f0c6e9e5fe4a}
haxxor
Category: Cryptography
Description
Encrypted string : 0x2-0x19-0x14-0x1d-0x1d-0x2a-0x9-0x61-0x3-0x62-0x15-0xe-0x60-0x5-0xe-0x19-0x4-0x19-0x2c
Solution
We’ll use xortool to solve this challenge. Delete all 0x and -, compliment single numbers with zeros to get 0219141d1d2a09610362150e60050e1904192c. Save it in a file (I used file.hex). The command should look like this
xortool -x -b -p "SHELL" file.hex
-x means that the input is hex-encoded, -b stands for brute-force and -p is for supplying known plaintext. Run the command and read the output to get the flag
SHELL{X0R3D_1T_HUH}
login
Category: Web
Description
Sam really need to get past this login portal but isn’t able too, can you help him? http://3.142.122.1:8889/
Solution
We see a standard login page. Inspecting the source or more specifically main.js we notice the username (din_djarin11) and some password hash (9ef71a8cd681a813cfd377817e9a08e5). We could try reverse engineering the hashing function, but to me it seemed too complicated. We can copy the hash into some hash analyzer (I used https://hashes.com/en/tools/hash_identifier). Our hash is probably MD5. Paste it into Crackstation to get the password - ir0nm4n. Log in, download the file and get the flag
SHELL{th1s_i5_th3_wa7_845ad42f4480104b698c1e168d29b739}
Under Development
Category: Web
Description
Solution
The only thing we can see after entering the site is the information, that it is still under development. After inspecting the source, we notice
We have a cookie! We can decode the contents of it (using CyberChef for example) if we simply use URL Decode and then Base64 Decode. The given string is user. Switch it to admin, encode with Base64 and supply to the cookie. Refresh and get the flag.
SHELL{0NLY_0R30_8e1a91a632ecaf2dd6026c943eb3ed1e}