dCTF
DragonEncrypted the flag I have
Hidden message
PowerPoint Programming
Very secure website
This one is really basic
Dragon
Category: Miscellaneous
Description
Hiding in plain sight
A file was attached.
Solution
The downloaded file is a .png, the dCTF mascot

After tweaking the image in Gimp for a while (or Photoshop), we can notice that the flag emerges after turning off red and green alpha channels and adjusting color levels
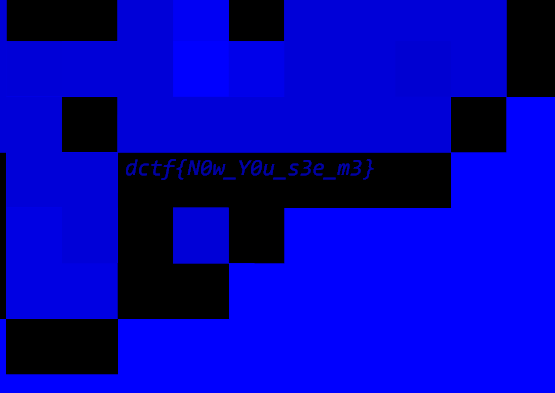
dctf{N0w_Y0u_s3e_m3}
Encrypted the flag I have
Category: Miscellaneous
Description
Decrypted flag is not in exact format
A file was attached.
Solution
The downloaded file looks like this

The title of this challenge seems out of order or if you watched Star Wars - it’s Master Yoda’s style of speech. Searching for star wars alphabet in Google we get what we’re looking for. Decode it letter by letter and get the flag
dctf{mastercodebreaker}
Hidden message
Category: Miscellaneous
Description
This image looks familiar…
A file was attached.
Solution
We’ll use a program called zsteg, used to detect hidden data in PNG and BMP. It can be installed with gem install zsteg or via GitHub. After running it, the first line in output returns our flag
dctf{sTeg0noGr4Phy_101}
PowerPoint Programming
Category: Miscellaneous
Description
A login page in powerpoint should be good enough, right? Flag is not in format. DCTF{ALL_CAPS_LETTERS_OR_NUMBERS}
A file was attached.
Solution
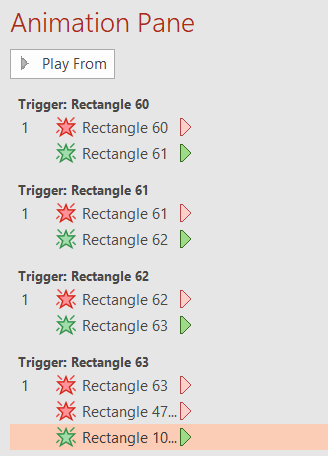
Downloaded file has a .ppsx extenstion, which means it is supposed to be read-only PowerPoint presentation. However, we can force the edit mode by opening PowerPoint -> Open -> chall.ppsx. In the Animations tab we can observe that some of the letters have little thunderbolts beside them. We can inspect the Animation Pane, to find a weird sequence
Clicking on it highlights some of the buttons

Starting at Rectangle 63 and going up letter by letter we can decode our flag
DCTF{PPT_1SNT_V3RY_S3CUR3_1S_1T}
Very secure website
Category: Web
Description
Some students have built their most secure website ever. Can you spot their mistake? http://dctf1-chall-very-secure-site.westeurope.azurecontainer.io/
Solution
So we are given the source code of the site
<?php
if (isset($_GET['username']) and isset($_GET['password'])) {
if (hash("tiger128,4", $_GET['username']) != "51c3f5f5d8a8830bc5d8b7ebcb5717df") {
echo "Invalid username";
}
else if (hash("tiger128,4", $_GET['password']) == "0e132798983807237937411964085731") {
$flag = fopen("flag.txt", "r") or die("Cannot open file");
echo fread($flag, filesize("flag.txt"));
fclose($flag);
}
else {
echo "Try harder";
}
}
else {
echo "Invalid parameters";
}
?>
We can decrypt the username hash (for example on this site) to get admin. The password is not as simple to crack. However, the code contains a vulnerability - the == sign can be exploited with Magic - specifically Magic Hashes. They can be found here. Search for tiger128,4 to get 479763000. Input it as the password and boom - we get the flag
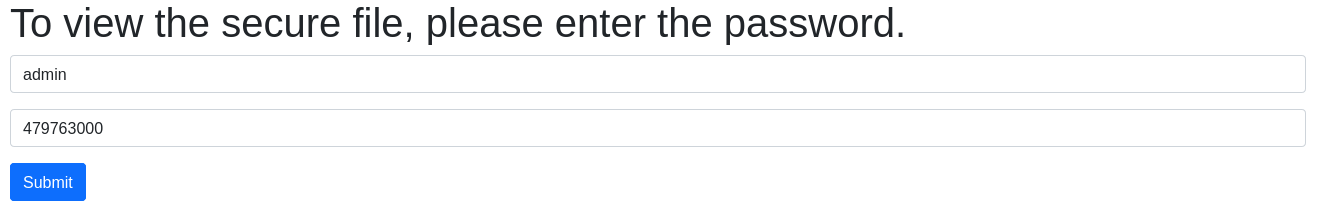
dctf{It's_magic._I_ain't_gotta_explain_shit.}
This one is really basic
Category: Cryptography
Description
The answer to life, the universe, and everything.
A file was attached.
Solution
The string in our file looks like Base64 encoded. One iteration is not enough, so we can do it manually with a tool like CyberChef or write a simple script to do it for us
import base64
message = open("cipher.txt").read()
while True:
try:
message = base64.b64decode(message)
except Exception:
break
print(bytes.decode(message))
We get our flag
dctf{Th1s_l00ks_4_lot_sm4ll3r_th4n_1t_d1d}